ghsa-g3cm-qg2v-2hj5
Vulnerability from github
Summary
Open redirect vulnerability due to incorrect validation of input values when redirecting users after login.
Details
pyload is validating URLs via the get_redirect_url function when redirecting users at login.
The URL entered in the next variable goes through the is_safe_url function, where a lack of validation can redirect the user to an arbitrary domain.
The documentation in the urllib library shows that improper URLs are recognized as relative paths when using the urlparse function. (https://docs.python.org/3/library/urllib.parse.html#urllib.parse.urlparse)
For example, When an unusual URL like https:///example.com is entered, urlparse interprets it as a relative path, but in the actual request it is converted to https://example.com due to url normalization.
PoC
-
In the next variable, insert the URL to which you want to redirect the user.
-
Check that it is possible to bypass url validation and redirect users to an arbitrary url.
Impact
An attacker can use this vulnerability to redirect users to malicious websites, which can be used for phishing and similar attacks.
{
"affected": [
{
"package": {
"ecosystem": "PyPI",
"name": "pyload-ng"
},
"ranges": [
{
"events": [
{
"introduced": "0"
},
{
"fixed": "0.5.0b3.dev79"
}
],
"type": "ECOSYSTEM"
}
]
}
],
"aliases": [
"CVE-2024-24808"
],
"database_specific": {
"cwe_ids": [
"CWE-601"
],
"github_reviewed": true,
"github_reviewed_at": "2024-02-05T23:23:22Z",
"nvd_published_at": "2024-02-06T04:15:08Z",
"severity": "MODERATE"
},
"details": "### Summary\nOpen redirect vulnerability due to incorrect validation of input values when redirecting users after login.\n\n### Details\npyload is validating URLs via the `get_redirect_url` function when redirecting users at login.\n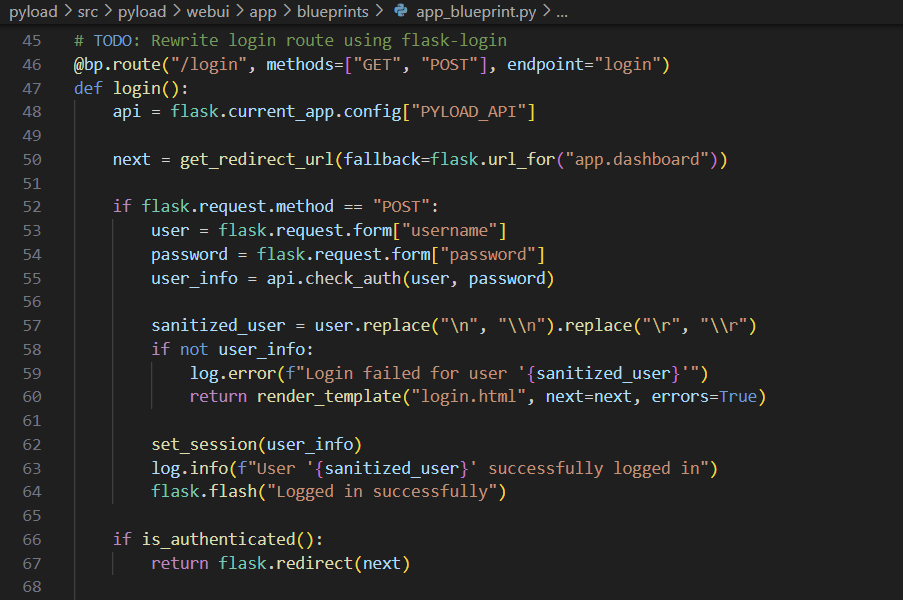\n\n\nThe URL entered in the `next` variable goes through the `is_safe_url` function, where a lack of validation can redirect the user to an arbitrary domain.\n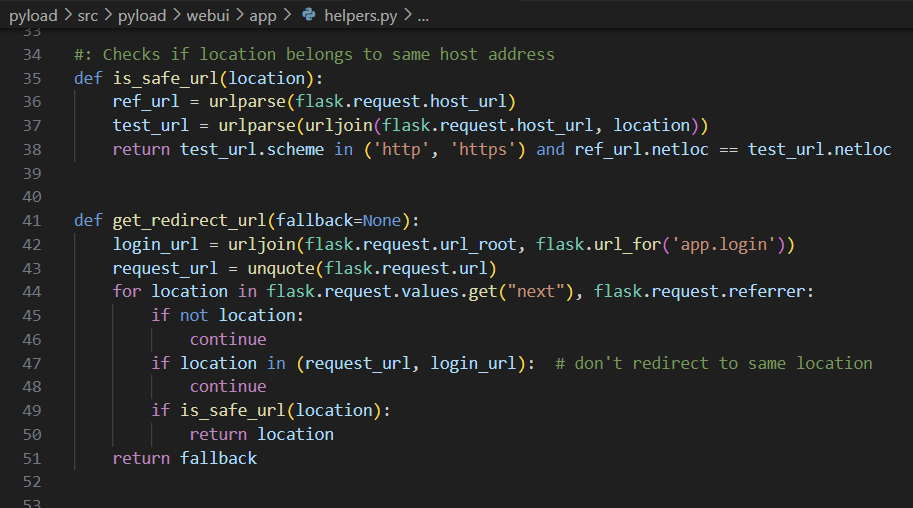\n\n\nThe documentation in the urllib library shows that improper URLs are recognized as relative paths when using the `urlparse` function. (https://docs.python.org/3/library/urllib.parse.html#urllib.parse.urlparse)\n\nFor example, When an unusual URL like `https:///example.com` is entered, `urlparse` interprets it as a relative path, but in the actual request it is converted to `https://example.com` due to url normalization.\n\n### PoC\n1. In the next variable, insert the URL to which you want to redirect the user.\n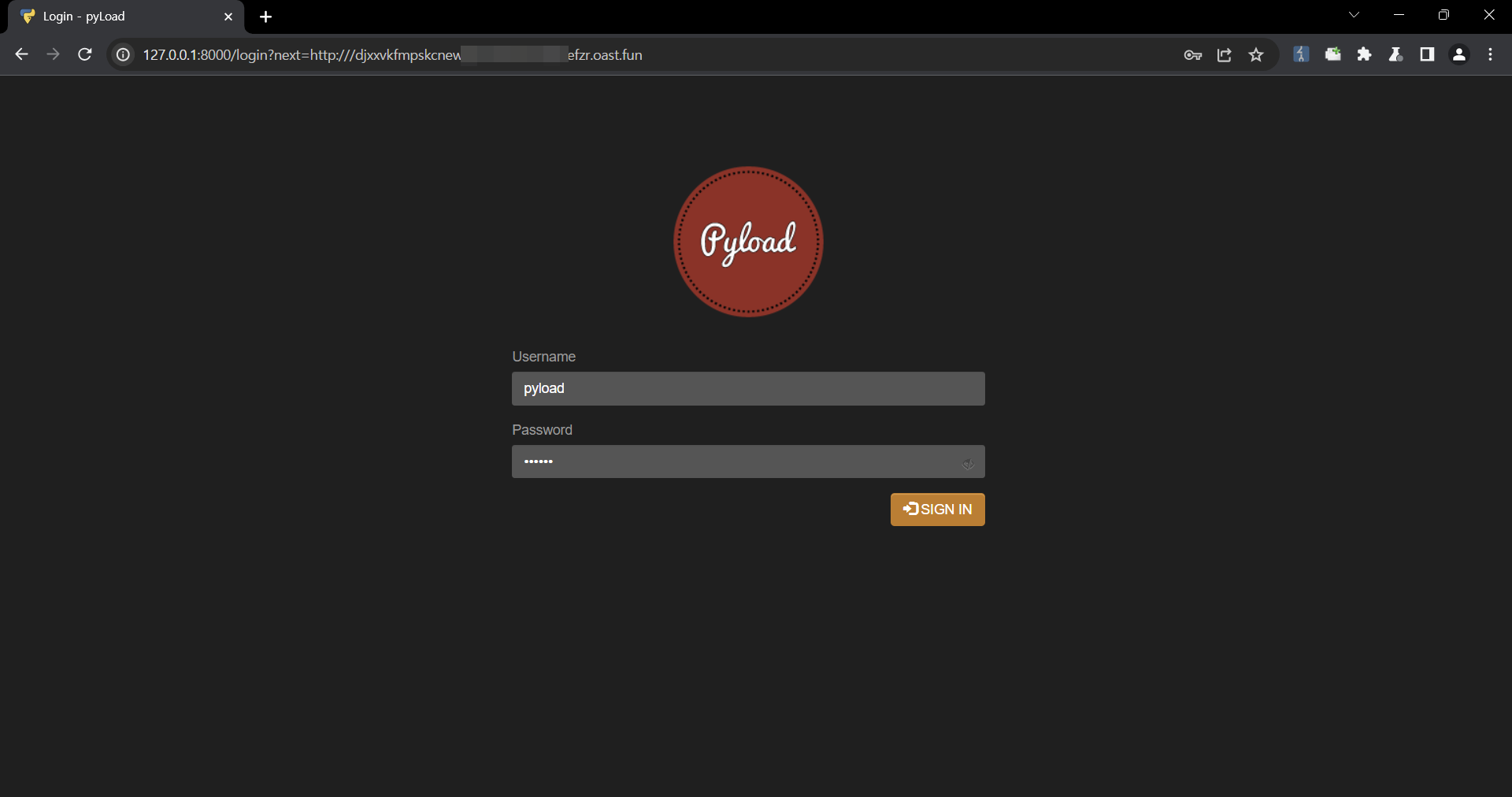\n\n\n\n2. Check that it is possible to bypass url validation and redirect users to an arbitrary url.\n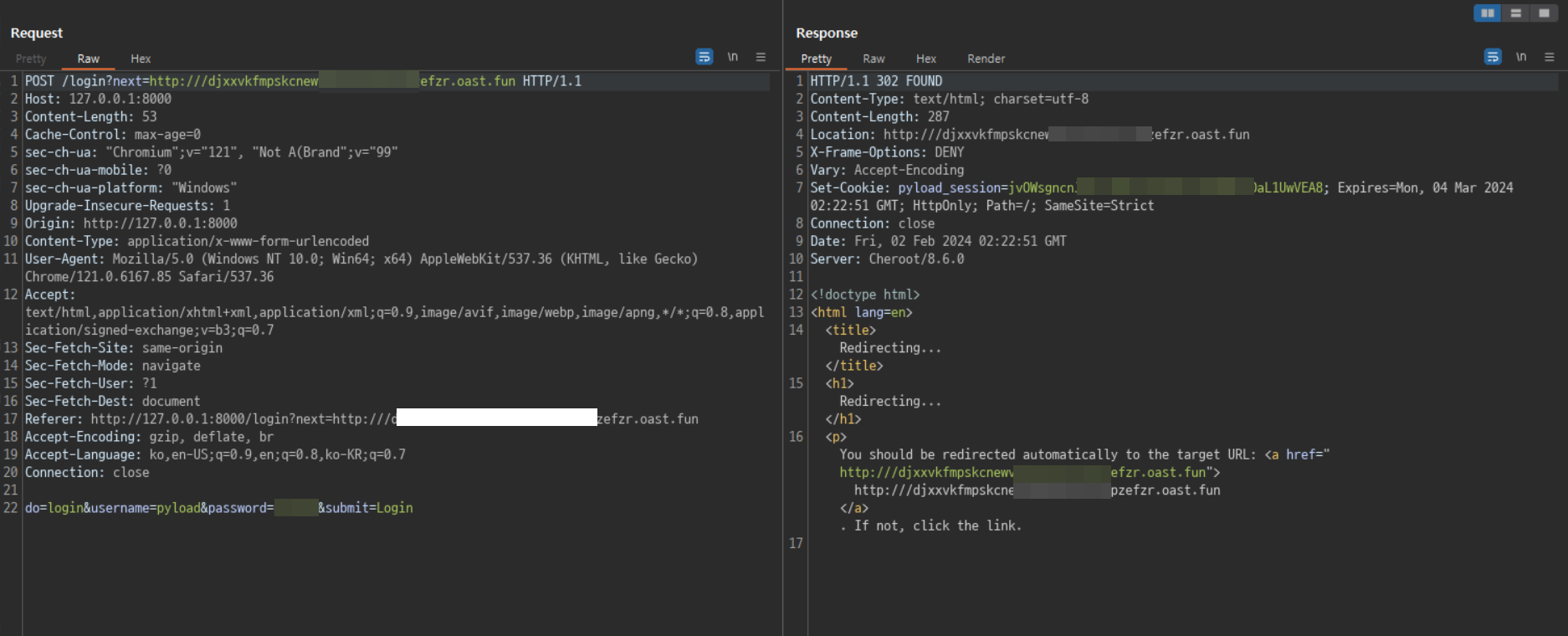\n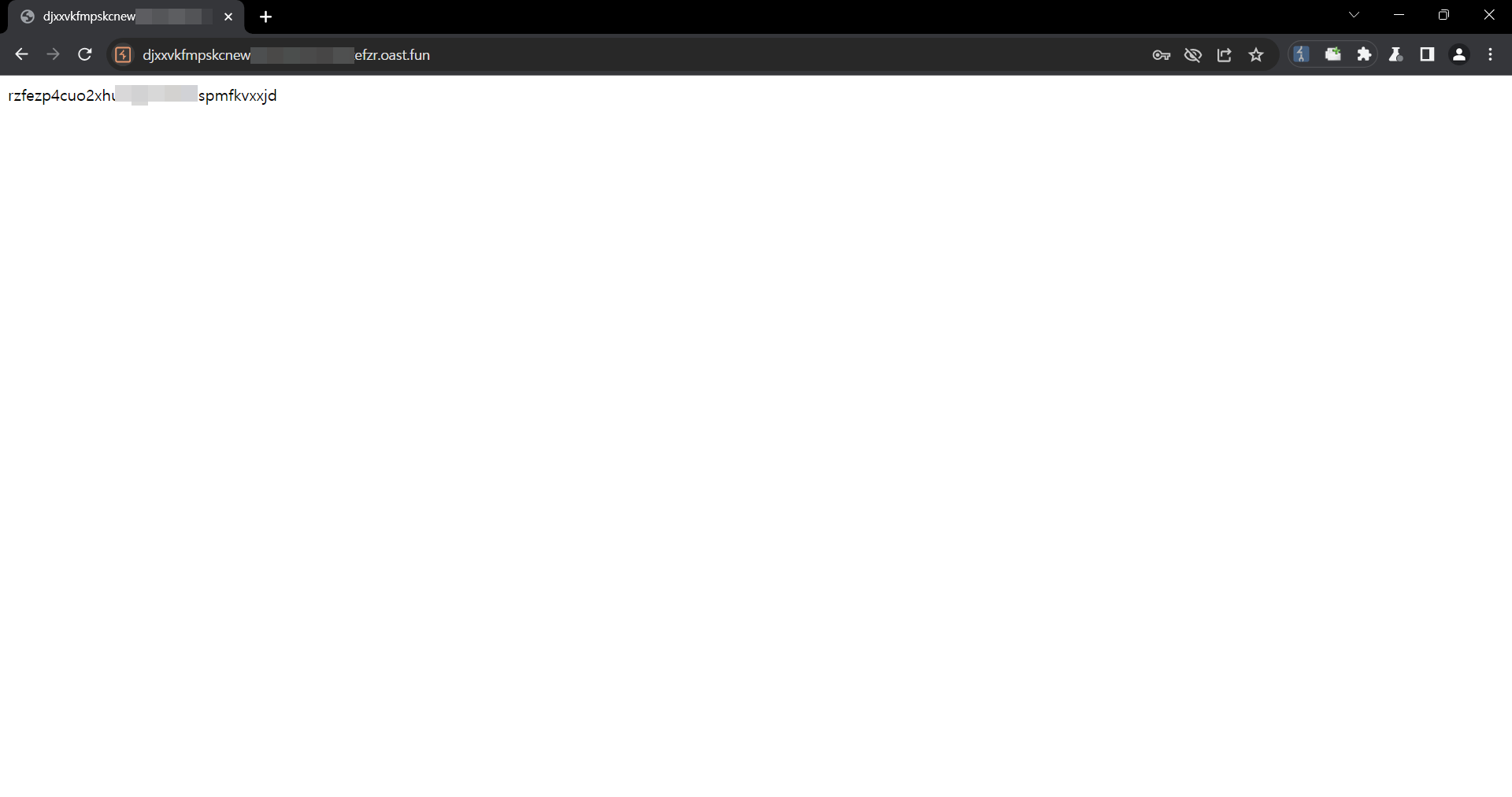\n\n\n\n### Impact\nAn attacker can use this vulnerability to redirect users to malicious websites, which can be used for phishing and similar attacks.\n",
"id": "GHSA-g3cm-qg2v-2hj5",
"modified": "2024-02-14T14:51:14Z",
"published": "2024-02-05T23:23:22Z",
"references": [
{
"type": "WEB",
"url": "https://github.com/pyload/pyload/security/advisories/GHSA-g3cm-qg2v-2hj5"
},
{
"type": "ADVISORY",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2024-24808"
},
{
"type": "WEB",
"url": "https://github.com/pyload/pyload/commit/fe94451dcc2be90b3889e2fd9d07b483c8a6dccd"
},
{
"type": "PACKAGE",
"url": "https://github.com/pyload/pyload"
}
],
"schema_version": "1.4.0",
"severity": [
{
"score": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"type": "CVSS_V3"
}
],
"summary": "pyLoad open redirect vulnerability due to improper validation of the is_safe_url function"
}
- Seen: The vulnerability was mentioned, discussed, or seen somewhere by the user.
- Confirmed: The vulnerability is confirmed from an analyst perspective.
- Exploited: This vulnerability was exploited and seen by the user reporting the sighting.
- Patched: This vulnerability was successfully patched by the user reporting the sighting.
- Not exploited: This vulnerability was not exploited or seen by the user reporting the sighting.
- Not confirmed: The user expresses doubt about the veracity of the vulnerability.
- Not patched: This vulnerability was not successfully patched by the user reporting the sighting.